Blogs and Articles
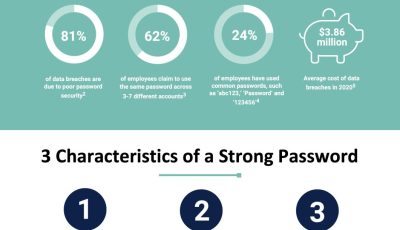
[INFOGRAPHIC] Protect Your Business with Good Password Hygiene
In today’s digital world, maintaining strong password hygiene is critical to safeguarding your business against cyberattacks. Did you know that 81% of data breaches are caused by poor password security? It’s easy to fall into the habit of reusing simple passwords, but cybercriminals are counting on that. With billions of dollars at stake, ensuring your […]
[Guide & Quiz] Unlocking the Potential of AI for Small and Medium-Sized Businesses
Let’s face it, science fiction robots might not be walking through the door just yet, but Artificial Intelligence (AI) is no longer a futuristic pipe dream. Today, AI is making waves in the real world, and not just for big corporations. Small and medium-sized businesses like yours can leverage the power of AI to streamline […]
[GUIDE] Which Cloud Model Is Right For Your Business?
Choosing the right cloud solution can feel overwhelming, but understanding your options is the first step to making an informed decision. There are two main paths to consider: building your own private cloud or leveraging a global cloud service offered by industry giants like Microsoft and Amazon. The Private Cloud Trap Many IT companies heavily […]
$97,000 Cyberattack Risk? Protect Your Business with These Proven Strategies
The average cost of cybercrime for small businesses has skyrocketed to $46,000, and for medium businesses, it increased to $97,000. These attacks can steal your data, lock you out of your systems, and damage your reputation – a chilling prospect for any business owner.
The CTO Role Outsourced: Unlocking Benefits for Mid-Size Companies
If you’re like most mid-size business leaders, your typical day probably includes several hours per week grappling with the IT needs of your business, without the guidance of an in-house tech leader. Enter the outsourced CTO (Chief Technology Officer) – a strategic solution that’s gaining traction. But what exactly does outsourcing a CTO entail, and […]
The Role of IT in Scaling Business Operations
We often speak to clients who are looking to scale their business but have not considered the role that IT can play in facilitating this. Typically, the focus is on increasing sales, expanding the workforce, or exploring new markets – all critical components, but it’s worth considering the role IT can play. At SMIKTECK, we […]
How to Make Smart IT Investments that Drive ROI for Your Business
As a business leader, you understand that technology is an essential tool for achieving a competitive edge and driving growth. However, navigating the vast array of tech options can be overwhelming. How do you ensure your investments deliver the desired return on investment (ROI)? At SMIKTECK, we understand the complexities of technology transformation. We’ve witnessed […]
[INFOGRAPHIC] Cybersecurity Starts with Your People
In today’s digital world, security awareness training isn’t optional – it’s the cornerstone of a strong cybersecurity strategy. With a staggering 85% of data breaches stemming from human error, your employees are a critical target for cybercriminals. Empower Your Team to Be Your First Line of Defence SMIKTECK’s comprehensive security awareness training equips your staff […]
Future-Proof Your Business with SMIKTECK: Tech That Grows With You
Whether you need cybersecurity support, managed IT, or a comprehensive IT strategy, we’re here to guide you.
Anticipating 2024: Key Trends in Managed IT Services
As we enter the 2nd quarter of 2024, it’s the perfect time to review the latest trends in the world of IT services. We continue to see businesses facing unique challenges presented by the rapid pace of technological advancements and the increasing reliance on digital infrastructure. The key to ensuring your operations remain seamless and […]
[INFOGRAPHIC] 15 Keys to Building an Unbreakable IT Disaster Recovery Plan
Every business needs a disaster recovery plan (DRP) – a roadmap to navigate unexpected downtime and minimize disruption. A well-crafted DRP can be the difference between bouncing back quickly or suffering crippling losses. This infographic unpacks 15 crucial elements you need to consider when building your IT disaster recovery plan, ensuring your business is prepared […]
Identity and Access Management (IAM): Your Cybersecurity Shield
Cybersecurity is a top concern for modern businesses. As attacks grow more sophisticated, Identity and Access Management (IAM) solutions have become essential. This infographic from SMIKTECK breaks down the crucial components of IAM, including multi-factor authentication (MFA), single sign-on (SSO), and privileged access management (PAM). Learn how IAM safeguards your business by ensuring only the […]
Bigger Isn’t Always Better: The Case for Boutique IT Service Providers
Tired of being lost in the shuffle with your IT provider? Do you feel like just another number? It’s time to ditch the “bigger is better” myth in IT. While large providers boast brand recognition and ample resources, promising security and reliability, their impersonal approach often leaves businesses longing for a different kind of service. […]
Be Prepared: The Importance of Business Continuity Planning
Ensuring business continuity is crucial in today’s unpredictable world. This infographic from SMIKTECK outlines the importance of having a business continuity plan in place and the steps you can take to create and implement one. The infographic highlights the high cost of downtime for businesses, emphasises the fact that many businesses are not prepared for […]
Beyond “Fix-It” IT Services: Future-Proof Your Business with SMIKTECK
Ensuring your technology works for you, not against you, is key to staying competitive and achieving your business goals. That’s where SMIKTECK comes in. We go beyond simply fixing IT problems. We offer a suite of managed IT services designed to future-proof your business. Whether you need robust cybersecurity, strategic IT consulting, or a complete […]
Managed IT Solutions: The Outsourced Advantage for SMBs
SMB owners have a lot to juggle at the moment. According to the Salesforce Small and Medium Business Trends Report, some of the most constraining factors on SMB operations right now include access to capital, finding the right technology to meet their needs, and hiring the right talent. Inflation continues to drive up business costs, […]
How SMIKTECK’s Tailored IT Service Fuels Newcastle Business Success
In 2024, it’s not just big corporations that need top-notch IT support – it’s your business too. Whether you’re charting diagnoses in a medical practice or building Newcastle’s next landmark, technology underpins every step of your success. But let’s face it, dealing with giant, impersonal IT companies can leave you feeling lost in the shuffle. […]
How Much Should You Be Spending On Cybersecurity?
The prospect of cybersecurity breaches presents more than just a technical challenge; it strikes at the heart of your daily operations, potentially leading to stressful downtimes that every business dreads. When systems go down, the ripple effect is immediate – customer demands go unmet, transactions halt, and the hard-earned reputation of your business comes under […]
The Cloud vs On-Site Server Question: What SMEs need to consider
In the cloud vs. on-site server debate, there is no simple answer. At SMIKTECK, we take an independent lens, analysing your business needs and workflows objectively to recommend the ideal mix of cloud and on-premise solutions, ensuring maximised value and seamless operations.
Don’t Let Your Inbox Host the Next Cyber Heist: Why Email Security Matters
Think your business email is safe? Think again. 90% of cyberattacks start in your inbox, with malware, ransomware, and phishing scams waiting to pounce. BEC scams alone cost businesses $2.7 billion in 2022! This isn’t just an IT problem – it’s a people problem. 82% of breaches involve human errors like clicking malicious links or […]
IT Service – Pay as You Go vs. Fixed Fee: Which is Right for Your Business?
Should you opt for the “Pay as You Go” (PAYG) model or embrace the “Fixed Fee” service approach? The choice can have a profound impact on your bottom line.
[INFOGRAPHIC] Protect your Business from Phishing Scams
Phishing scams are a type of social engineering cyberattack in which criminals send emails that appear to be from a legitimate source, such as a bank or government agency. The goal is to trick the recipient into clicking on a malicious link or opening an infected attachment, which can then install malware on their computer […]
[INFOGRAPHIC] 15 Ways to Protect Your Business from a Cyberattack
Cyberattacks are a serious threat to businesses of all sizes. In fact, according to a recent study, 1 in 5 small businesses will suffer a cyber breach this year. The consequences of a cyberattack can be devastating. Businesses can lose sensitive data, suffer financial losses, and even be forced to close their doors. That’s why […]
Shifting the Paradigm: From IT Cost to Strategic Investment
In today’s rapidly changing business environment, IT has become increasingly important, but some CEOs and business owners still see it as a cost centre, a necessary expense that does not contribute to the bottom line. In this article, we outline how this outdated perception can lead to dire circumstances at worst, and how in an […]
[INFOGRAPHIC] The Essential 8: A Guide to Cyber Security for Australian Businesses
The Essential 8 is a set of eight cyber security mitigation strategies designed to help organisations defend against cyberattacks. These strategies are essential for small and medium-sized businesses, as they are often the targets of cyberattacks. The infographic provides an overview of the Essential 8, including: What the Essential 8 are Why they are important […]
Work together, anywhere with an Ericsson LG iPECS Phone System
Have you thought about upgrading or refreshing your business communications system? Have you thought about a cloud communication solution? In an age of ever improving technology solutions the need to keep our phones ringing and connection to our customers has never been more important. Clearly some communication solutions are better than others, like the image […]
Don’t fall victim to this new scam: learn how to identify and prevent it
At Smikteck, we take the security of our clients’ information very seriously. Unfortunately, we have noticed an increase in phishing scams and man-in-the-middle tactics targeting CEOs and CFOs to bypass two-factor authentication (2FA) or multi-factor authentication (MFA) logins. This has become a global problem affecting millions of users and some of the biggest companies on […]
Cyber Safety During the Holiday Season
Holiday cyber security should be at the forefront of our minds as we approach the holiday season. We may be a little less focused on security as our thoughts turn to holidays, family and food. It’s the drop in security focus that gives cybercriminals easier access. Before you lock the door of your business on […]
What does “No Lock In Contract” actually mean?
You may have noticed that we are always talking about “no lock in contacts” at SMIKTECK. But what does that actually mean and why is it a benefit to me and my business? At SMIKTECK we don’t have any contract with our clients. That means that we are backing ourselves to provide high […]
Password Managers
Do you use a password manager to create and save your passwords? A Password Manager is a program that stores, generates and manages your passwords. It is a secure program that stores passwords in an encrypted environment. Using a Password Manager to generate and securely store your passwords is SMIKTECK’s Top Tech Tip of the […]
Cyber Security Awareness Month
October is Cyber Security Awareness Month. During this month we are asked to focus on the security and safety of our technology environment and our on-line activities. With so many cyber attacks leading to data breaches impacting thousands of users clogging media channels it’s no wonder our on-line security is in focus. So, how do […]
Technology is at the HEART of healthcare
IT helps build community health At a time when most IT professionals were retreating to remote workplaces, local IT experts Smikteck were hitting the road to support Aboriginal health care provider, Awabakal, to provide remote vaccination clinics and 12 months on, they are ready to share their lessons learnt with other medical services. Smikteck Director […]
Keeping Your Technology Healthy
Strong, secure and healthy technology is an important part of any business operation. More and more we see business owners viewing technology as a business investment not just a necessary evil. The understanding that technology can hold the key to improved productivity means that it is more and more important as a major part of […]
Cyber Security Awareness Over Holiday Periods.
During holiday periods cyber criminals tend to increase their activities. This is generally due to the fact that while we are all relaxing and enjoying some down time away from the confines of the office we may be less meticulous with our security measures. Cyber criminals take advantage of holiday periods and our lack of vigilance as […]
How would Microsoft Azure work for my business?
What is Microsoft Azure? Microsoft Azure is a cloud based storage solution which allows business to move away from in-house servers to a more secure and flexible cloud solution. What does Azure migration mean? Migrating to Microsoft Azure means that all data held on-site is migrated or transferred to secure cloud based servers. Access to data is streamlined […]
What is Multi-factor Authentication and why do I need it?
Multi-factor Authentication or MFA is an added security measure creating a higher level of protection for technology environments. When logging in users are prompted to enter a code which is sent to a separate device or a code from an authenticator app. Multi-level security ensures that gaining access to a password is not enough for […]
What is cyber security awareness and why is it so important?
With October being Cyber Security Awareness month, we wondered how security aware you and your team really are. What is Cyber Security Awareness and why is it so important? Cyber security awareness is about your awareness of the cyber threats that your technology environment may be at risk of. Being aware of the risks and […]
How we support you during change
How we support you during change Recently I discussed the pain of change and how simple it can be once the first step was taken. A huge factor was the support I had during the changes I made. So I want to share how SMIKTECK can support you in times of change. With a […]
5 Reasons to Audit Technology
5 Reasons you should have your technology operations audited Audits can make the most seasoned professional hide in the corner. At SMIKTECK we prefer to look at audits in a much more positive light. We see audits as a way to continuously improve your technology and ensure it’s aligned with your business operations. Here are the 5 most important reasons to have your technology […]
What actions are we taking?
COVID-19 There a lot of mixed messages and opinions travelling around so it can be difficult to know what to do with the current position of the COVID virus. What are we doing at work? Keeping a 1.5m distance where possible Wearing a mask when out of our homes Keeping a mask on hand at […]
The pain of change
The Pain of Change There are a long list of things that go into my too hard basket – changing banks, switching insurances, finding a new hairdresser, upgrading my phone, going to a new gym, changing jobs or even trying the new local for dinner. My thoughts behind it – if it’s not broken, don’t […]
What has COVID-19 taught us about Technology
What has COVID-19 taught us about Technology COVID-19 has surely made an impact to all of our lives. Day to day tasks that we took for granted are suddenly actions that need to be considered.Shopping for essentials, being timed at your favourite restaurant, restricted from seeing loved ones and searching for those small local […]
Keeping your business safe.
Keeping Your Business Safe Over the past couple of weeks we have talked to you about what severe impacts unsafe or unsecured Wi-Fi can have on your business. It can be a time consuming and painful process should something go wrong and could have financial and reputation damage to your business. Let’s look at […]
Data Breach Reporting
What is a Data Breach? We’ve recently shared information about how frequently large Australian companies are falling victim to data breaches, in fact, according to OAIC’s latest report, notifications of data breach have increased by 19% and a total of 537 reports were made between July-December 2019.A data breach is when there is unauthorised access […]
Wi-fi – Is it dangerous?
How secure is your Wi-Fi? Wi-Fi is a wireless networking technology that uses radio waves to provide high speed internet. Having a good wi-fi connection allows computers, mobile devices and other types of technology to connect to the internet wirelessly. Convenient, Yes! Risky, also Yes! We have to ask the question, what are people […]
How are you staying connected?
How are you staying connected? Working remotely, or from home can be difficult. When we’re forced to make changes to the way we operate we can often feel uncomfortable and fearful. We’ve been working hard to find ways to make sure that not only our own team but all of our clients are able […]
Technology Strategy Consultation
At SMIKTECK we love a good story, especially when it is about one of our valued clients. Recently we had the great experience of rolling out our new technology risk audit and consultancy service for a wonderful Newcastle based charity. After auditing all of their sites, we compiled a report detailing; Technology strengths, Weaknesses, Risk […]
5 Ways to Improve Your Business Internet
Getting your business online is one thing, but could you be doing it faster, or better? Here are 5 ways you can improve your business internet at work. 1. Faster Wi-Fi for your business Improving your Wi-Fi connection is probably the simplest way to speed up your business internet. Wi-Fi can be incredibly fast, when […]
4 Steps on how to choose a server
A server can either help your business to become more efficient or be a potential bottleneck. Here’s how to choose a server and make sure you have access to enough storage (no more traffic jams) without overpaying. 1. What do you need a server for? The intended use is what matters most. Knowing what you […]
Safeguarding Your Small Business from Theft
All businesses are vulnerable to theft, but did you know that small businesses may be more susceptible to data theft than their larger competitors? Small businesses are less likely to have the right security controls in place to keep their information safe. You only need to make a few small adjustments to safeguard your business information from […]
7 Sure Signs You’ve Been Hacked
Antivirus software is important… but there’s only so much it can do to protect you from hackers determined to access your information. So, how can you tell if you’ve been hacked? Do you know what to look for? 1. Unwanted items pop up on your screen— like toolbars on your web browser, unexpected pop-ups, or new programs […]
Emerging Tech Trends 2017
Welcome back to work. It’s time to grab your first coffee and start thinking about the major trends, opportunities and challenges for the year ahead. It’s going to be another whirlwind year The pace with which technology is advancing means that change is a constant. Continual improvements in processing power, cloud and data storage, and […]
Holiday Hackers: 4 Ways You’re Vulnerable this Silly Season
Your kids are not the only ones counting down the sleeps until Christmas. While the little ones are dreaming of Santa filling their stockings with presents, cyber criminals are scheming new ways to line their pockets. 1. Gone phishin’ When your staff go online shopping at their work desks, they could be putting their bank […]
What Does This Image Have to Do with IT?
A frog wearing a top hat, smoking a cigarette. What, you might ask, does this have to do with IT? The Smikteck blog has been up and running for a few months now, and some of our clients have been asking about the weird and wonderful images accompanying our stories. Here’s the inside scoop. You […]
3 Things You Need to Know About… the Cloud
Cloud technology is used by most people, every day. Yet most people don’t know the basics. Here are the three simple things you should know about the cloud. The name is misleading Because we don’t physically see ‘the cloud’ when we use it, it’s easy to forget that it’s actually a network of physical servers, […]
Recovering From Data Loss
Accidentally deleted documents. Intentional hacking. Hard drive failures. Power black outs. Software bugs. There are all sorts of ways you can lose data. According to the 2016 EMC Global Data Loss and Protection Index, 71 % of Australian organisations are still not fully confident in their ability to recover after a disruption. So how can you beat the […]
9 Steps to Stop Hackers Hurting Your Business
Losing data to online hackers can cost your business dearly. Big or small, Australian businesses need to take preventative measures to protect themselves and their customers from cyber threats. While there are personal measures we can all take, such as managing passwords and avoiding public Wi-Fi use, companies need to take a bigger-picture approach to […]
Telstra Customer? How & Why You Should Disable Telstra Air
If you’re a Telstra Internet customer, you’re now broadcasting a free and unsecured WiFi network. You should disable it. Yes, you read that right. Since 1 July 2016, Telstra Internet customers have been subject to broadcasting a free and unsecured WiFi network via their Telstra Broadband (NBN and ADSL) modem/router. It’s called Telstra Air. Anyone who […]
3 Ways to Insure Against Cryptolocker Ransomware
Cryptolocker continues to pose a huge threat to individuals and organisations in Australia and beyond. It’s been around in various guises for more than 15 years, outliving many genuine businesses. In fact, a recent Australian Government report claimed that 60 per cent of businesses hit by a cyber-attack go out of business within 6 months. The same […]